New Presidential Policy Directive 21 (PPD 21) “Kicks the Can” on Critical Infrastructure Protection

On February 12th President Obama released Presidential Policy Directive 21 in conjunction with his State of the Union Address. PPD 21 directs the Department of Homeland Security to work with critical infrastructure owners and operators, federal agencies that oversee critical sectors (SSA’s or sector-specific agencies), and State, Local, Tribal and Territorial governments (SLTT’s) to protect critical infrastructure from attack or disruption. The new policy recognizes the importance of cybersecurity in critical infrastructure protection, which the 2009 National Infrastructure Protection Plan does not address as vigorously. It also establishes “national critical infrastructure centers” in the physical and cyber space designed to promote information sharing and collaboration. Additionally, the policy orders the State Department to be engaged with DHS on issues of international interdependencies and multi-national ownership, growing concerns of the global economy.
But PPD 21 is just as interesting for what it includes that isn’t new, and much of it is not new. It raises several questions about what progress has been made over the past 5-10 years, and why the Obama Administration feels the need to reset the timer.
For example, PPD 21 requires DHS to “identify and prioritize critical infrastructure” as an “additional role and responsibility”. But DHS has been doing this for years. In 2003 I received a phone call from a DHS contractor. As coordinator of state-owned infrastructure, I must have made some list of contacts given to a (probably Booz Allen) contract DHS employee. I was asked a series of questions regarding critical infrastructure in my jurisdiction. The information was needed, according to the contractor, because the Department of Homeland Security was compiling a state-by-state list of critical infrastructure. In the years since, I have submitted revisions and updates to my “Tier 1 and Tier 2” lists of sites. The Government Accountability Office (GOA) describes this process this way in a 2010 report:
“The process of identifying these nationally significant assets and systems is conducted on an annual basis and relies heavily on the insights and knowledge of a wide array of public and private sector security partners. CIKR categorized as Tier 1 or Tier 2 as a result of this annual process provide a common basis on which DHS and its security partners can implement important CIKR protection programs and initiatives, such as various grant programs, buffer zone protection efforts, facility assessments and training, and other activities. DHS has other tiered categories of infrastructure whose destruction or disruption would not have a significant national or regional impact, though local impacts could be substantial.”
DHS’ “additional roles and responsibilities” also includes the development of vulnerability assessments on CI/KR, which they have also done for years via their Protective Security Advisors. These efforts are aimed at meeting the risk management goals of prioritization and the establishment resource allocation priorities via programs such as the Buffer Zone Protection Program. The list of “additional roles” within PPD 21 for DHS goes on to include providing informational support, coordination with Federal departments on prosecutorial issues, and mapping. All of which are old news.
PPD 21 does little to enhance the CI/KR resilience programs already in existence. And while movement toward cybersecurity and a nod to the national continuity directives are helpful, they are also kind of obvious. These are simple adjustments not grand new (State of the Union announcement!) plans. It will be interesting to see what comes of the “national critical infrastructure centers”, and we look forward to reading the annual reports. But in the end, PPD 21’s most significant contribution to improving the National Infrastructure Protection Plan might be the removal of the National Monuments and Icons and Postal and Shipping sectors. No one was quite sure what to do with those. Make Mount Rushmore more resilient or teach UPS how to manage emergencies?

We have said here that we are not quite sure what “Homeland Security” is, particularly at the local level. Now a new report from the Congressional Research Service (CRS) says that ten years after the 9/11 attacks the federal government still does not have a concise definition for homeland security. The brief report is unambiguous as it points out the strategic repercussions of the lack of agreement on the scope and function of homeland security. Consider this passage from the report’s summary:
“Varied homeland security definitions and missions may impede the development of a coherent national homeland security strategy, and may hamper the effectiveness of congressional oversight. Definitions and missions are part of strategy development. Policymakers develop strategy by identifying national interests, prioritizing goals to achieve those national interests, and arraying instruments of national power to achieve the national interests. Developing an effective homeland security strategy, however, may be complicated if the key concept of homeland security is not defined and its missions are not aligned and synchronized among different federal entities with homeland security responsibilities.” (p. 2)
The report discusses the evolution of the homeland security enterprise in the various strategies and reports that have been published since 2001 and discusses the implications of the lack of consistency on the nation’s overall homeland security strategy. A highlight of the report is a useful table on page 8 entitled “Summary of Homeland Security Definitions”. It provides an overview of the pertinent homeland security strategic plans and their associated definitions for “homeland security”. This table should be required reading in every Introduction to Homeland Security course.
An opportunity exists to augment this report by discussing the implications of homeland security ambiguity to state and local governments, universities and the private sector. States and local governments must implement programs related to homeland security in support of the national effort. State and local government officials need a thorough understanding of the stated goals of homeland security in order to provide that support. Further, colleges and universities are developing programs that provide degrees in homeland security. Without a clear understanding of what homeland security means, it will be difficult to fully prepare the next generation to fill strategically important roles in the enterprise. And businesses across the country are developing products and services to serve a discipline that could stimulate the economy. But to be successful these businesses need clarity of the mission.
The essential problem is summarized very concisely in the following passage from the analysis section of the report:
“Homeland security is essentially about managing risks. The purpose of a strategic process is to develop missions to achieve that end. Before risk management can be accurate and adequate, policymakers must ideally coordinate and communicate. That work to some degree depends on developing a foundation of common definitions of key terms and concepts. It is also necessary, in order to coordinate and communicate, to ensure stakeholders are aware of, trained for, and prepared to meet assigned missions. At the national level, there does not appear to be an attempt to align definitions and missions among disparate federal entities. DHS is, however, attempting to align its definition and missions, but does not prioritize its missions; there is no clarity in the national strategies of federal, state, and local roles and responsibilities; and, potentially, funding is driving priorities rather than priorities driving the funding.” (p. 13)
Our compliments to the CRS and analyst Shawn Reese for a hard-hitting report that doesn’t mince words. We at Homeland Security Roundtable hope it gets the attention it deserves.
In a recent conversation with a state/local homeland security professional, a discussion about the relationship between cybersecurity and homeland security began with a compelling story about the early days, when homeland security was just emerging from the ashes of 9/11. Tom Ridge was, like William “Wild Bill” Donovan in the early days of WWII, building a new government agency to defend the country. White powder near the coffee maker or on the table where the powdered donuts were eaten yesterday was resulting in calls to 911. And concepts like “critical infrastructure protection” and “public-private partnerships” were becoming popular priorities…
“…I was appointed my agency’s representative on our states “homeland security task force”, so I was doing that plus my regular job which at that time hadn’t changed much. I remember clearly getting an email (back in those days I didn’t get as many so I could actually remember them). The email said that my agency was being awarded a grant of $100,000.00 for homeland security projects. Just like that. Here’s a hundred grand. Spend it. A few years later I applied for and was awarded over $2 Million in one year for my agency’s projects. Then we had a process but it was manageable. A couple of years after that, the process started getting heavy. Lots of red tape, lots of detailed submittals. And there was more competition and a rigorous application and selection process. Around 2008 it began to get downright difficult to find time to get the regular job done. Now, the money is almost non-existent, but the hassle remains and then some. So if you want to know what is keeping us from pulling out of the homeland security enterprise all together, I’ll tell you. First, we want to remain at the table and have access to collaborative opportunities and information. Second, cybersecurity. Our networks are being attacked all day everyday and our systems are vulnerable. Cybersecurity is the new homeland security and we are afraid of missing out on opportunities to get help.”
The phrase “cybersecurity is the new homeland security” was the impetus for a brainstorming session that resulted in the following five ideas or concepts associated with the relationship between cybersecurity and homeland security. We did not necessarily set out to answer any questions or decide on any outcomes, but we found the conceptual discussion provided great opportunities for research and discussion:
- Cybersecurity is a Part of Homeland Security – Cybersecurity may be a part of one sector of the homeland security enterprise. In the National Infrastructure Protection Plan it would likely fall somewhere within the Information Technology sector. However if that is true, it may be currently the only sector that matters. Toss out the sectors that haven’t been attacked today, or this week, or this month, and you are left with IT. And with all of the other sectors relying on IT systems to operate, why do we need the rest of the plan? (It’s a conceptual question.)
- The Bad Guys Are in Cyberspace – With drones buzzing overhead waiting for the bad guys to look up or worse, make a phone call, what better way to keep up the attack on the US then staying underground and anonymous. No need to go to the airport with a thousand cameras watching your every move. The Israelis have you profiled before your bags are out of the trunk. Just pick a cool online handle and bounce your IP through Iran. You’ll be probing US drinking water systems or the power grid by lunch.
- Cyberspace is All-Hazards – A few years into the homeland security enterprise “all-hazards” became a buzzword. It was followed by “resilience” and the current “whole community“. But homeland security should be an “all-hazards” enterprise, and cybersecurity certainly fits the bill. Cyberspace is rife with not just terrorists but, more abundantly, everyday criminals. Cybersecurity offers an unparalleled opportunity for the all hazards approach, and any agency involved in cybersecurity operations must operate to root out crime and terrorism. That’s worth funding with grants. And that’s why Director Mueller is focused on cyber.
- Homeland Security is Still Vague and Nebulous, Cybersecurity is Not -We know it is a recurring theme here at HLSR but we still don’t completely understand what “homeland security” really entails or how well most homeland security degrees prepare students to enter the workforce. However give me a BS in Network Security from an accredited school and I’ll give you a job.
- The Energy and Excitement Factor – The energy and excitement is in the Cybersecurity area today just as it was in the homeland security area in 2002. However the trends all point to a longer and more drawn out fight in cyber as computers become more and more a part of everything we do – cybersecurity may outlive homeland security. One litmus test is, “What is Congress currently unable to agree upon?” They have been most recently unable to pass some much needed cyber legislation, so states are getting more involved. That means that whether Congress acts or not lots of energy, excitement, money and jobs are in the field of cybersecurity, while the Homeland Security Grant Program fizzles and the Urban Area Security Initiative downsizes.
We’re not giving up on homeland security, and an “all-hazards”, “resilient”, “whole-community” approach is necessary in the long term. Tactics will evolve and too much focus in one sector will surely leave us vulnerable. But there is no denying the fact that thousands, probably millions of attacks occur daily on US infrastructure via the computer networks. If the Department of Homeland Security truly focuses on risk, there will be a laser focus on cybersecurity for years to come.
“This is the way the world ends. Not with a bang but a whimper.”
~ T.S. Eliot, The Hollow Men
_________________________________________________
“Portland Tower, NW flight 337 heavy”
“Flight 337, Portland Tower”
“Portland Tower, flight 337, we are experiencing instrument inconsistencies. Could you give us your read on our altitude and location?”
“Flight 337, are you declaring an inflight emergency?”
“Negative Portland, we just want to validate what are instruments are telling us.”
“Flight 337, we have you at 4-7-thousand about 100 miles west of Boise, at 490 knots.”
“Portland, be advised, we will need your assistance until otherwise notified. Instruments have us at mach 3 entering Canadian airspace.”
Not the only problem noted, but one of the first recorded. Aircraft throughout the west coast begin reporting similar instrument failures. The Air Traffic Controllers quickly push the issue up the chain, and the FAA, in consultation with the DHS and the President, grounded all flights over California, Oregon, Washington, Idaho, Montana, Utah, Arizona, Nevada, Alaska and Colorado.
Verizon, AT&T, and Sprint, became flooded with notices that cellular phones were inoperative. All carriers receive similar reports. The same collection of western states is now plagued with lack of wireless service, and land-based communications are soon overwhelmed.
Many hospitals began reporting that their medical paging systems were no longer operational. ATM’s all over the west coast were no longer amenable to giving you your hard earned cash. The ports of Los Angeles, Long Beach, San Diego, Seattle/Tacoma, and San Francisco lose the ability to track ship traffic, and cargo had to stay ocean bound while a low tech solution was used to allow ships to safely enter and leave the ports. On ship gyroscopes were giving ship’s navigators inaccurate readings, as the gyros are calibrated using GPS. Many cargo ship captains choose to stay far out at sea for fear of hitting other vessels. Anti-collision digressed to visual spotters and binoculars.
Rail traffic slowed to 10% of capacity, as the presidentially mandated Positive Train Control (PTS) caused collisions and near collisions by reporting train location data incorrectly.
Rolling blackouts began to occur as electrical grid operators were no longer able to synchronize power with other grid dwellers. To make matters worse, some of the smaller electrical suppliers began suffering Aurora Vulnerability failures.
Likewise, water and sewer operators began suffering catastrophic failures of large electric pumps, again from Aurora Vulnerability. Domestic water service was spotty, and waste water began exploiting emergency overflow plans, causing contamination and potential disease issues.
Industry officials reported that the software addressing Rockwell International Programmable Logic Circuits (PLC), the most common PLC in use in America and commonly used in SCADA (supervisory control and data acquisition) controls had malfunctioned. The result was physical destruction of the pumps and generators.
Social media spreads the word about inaccessible ATM machines. By the time banking hours rolled around, people fearing their lack of ATM access to their cash began drawing out large sums. Retailers start moving towards cash only transactions. Civil disturbance became a potential issue for local law enforcement.
The military began a flurry of activity to mitigate the impact of these occurrences on their Power Projection capabilities. A Power Projection Platform (PPP) is “an Army installations that strategically deploy one or more high priority active component brigades or larger and/or mobilize and deploy high priority Army reserve component units.” This disruption has taken out PPP for three key locations: San Diego, Tacoma, and Colorado Springs. Even the remaining 12 platforms were degraded, as the cascading effect of crippled west coast rail traffic slowed rail traffic to east coast sea ports.
The Air Force was concerned about air sovereignty for a significant portion of the US land and sea border. The Navy was repositioning ships, but cautiously due to the increase of directionless cargo ships. As the military scrambled to find answers, they discovered that five (5) GPS satellites had been “spoofed” which alters the satellite’s transmission from their internal atomic clocks. The result is inaccurate positioning data. Much worse, the GPS clock data is used for cell phone tower coordination, electrical grid synchronization, gyroscopic system validation, stock market fraud prevention, and many other infrastructure systems. Just knowing you are being spoofed does not provide immediate relief. Since the GPS signal is spoofed after it leaves the satellite, the fix is not at the satellite. The spoofing has to be stopped.
Once the news of the spoofing leaked out, unscrupulous stock traders tried to exploit the time inaccuracy to leverage advantageous stock purchases. If you know in advance a stock is going up, and you can use the time inaccuracy to “back date” your purchase, you can win every time. The New York Stock Exchange closes until the vulnerability can no longer be exploited.
The net result is economic crisis, transportation gridlock, much of the west coast population is challenged by a lack of water, power and sewer, degraded military capability, crippled supply chain, disrupted crop cycles (irrigation), and lack of capacity for just-in-time perishable commodity delivery.
___________________________________________________________________________________________________________
In designing this scenario, I limited myself to existing technology, capabilities, and conditions. I have cited references for those who disbelieve or want more information. An attack of this magnitude would require the sophistication and resources of a nation state. I assert this is the same formula that describes the STUXNET attack on the Iranian nuclear centrifuges. The technology in the scenario already exists, and is, generally speaking, readily available. One of the additional advantages of a cyber-based attack is that none of the cited technologies allows for easy attribution. Against whom do we retaliate?
GPS spoofing has already occurred, both intentionally and unintentionally. Allegations were made that North Korea jammed the GPS signals near the North/South border. Although denied by the North, the following advisory came out to pilots operating in the area:
CAUTIONARY INFORMATION FOR AIRCRAFT OPERATING IN INCHEON FIR:
PILOTS HAVE REPORTED THAT GPS SIGNALS ARE UNRELIABLE OR LOST INTERMITTENTLY IN INCHEON FIR.
EXERCISE EXTREME CAUTION WHEN USING GPS. 28 APR 00:32 2012 UNTIL 03 MAY 15:00 2012 ESTIMATED.
CREATED: 28 APR 00:34 2012.
Of course the criminal element would not want to miss out. Here is a quote describing the economics GPS spoofing: “Criminals could also spoof GPS timing for profit. The US National Association of Securities Dealers requires financial traders to time-stamp transactions with an accuracy of within 3 seconds. The bad guys would spoof the timing at their preferred site and, watching an upward trend, buy stock a few seconds in arrears,’ says Humpreys. ‘Those three seconds could be worth a lot of money.”
Another GPS disruption impacted the San Diego area. Traced to a US Naval exercise, it impacted GPS navigation, ship tracking, ATMs, cell phones, and emergency medical paging. GPS jamming on a smaller scale is both cheap and easy, thanks to internet retailers. Truck drivers who don’t want their bosses to know where they are can jam the signal coming from their truck. Some toll roads use GPS as part of the toll system. Jammers can provide a free pass through the toll gate.
We have become very reliant on GPS, not just for navigation, but for that precise internal atomic clock that is necessary for GPS to work. The technologies that rely on that clock are varied. For example, the ability of electrical grid operators to synchronize the electricity on the grid from multiple generation sources is essential for inter-system electricity distribution. This synchronization is done with GPS.
There is a system that provided an alternative to GPS navigation. Called eLORAN, it is still used in many countries, but is being abandoned in the US, leaving us no alternative to GPS.
GPS is also an essential part of the Positive Train Control system (PTC). The Rail Safety Improvement Act of 2008 (RSIA) (signed by the President on October 16, 2008, as Public Law 110-432) has mandated the widespread installation of PTC systems by December 2015.
Let us not forget that many of the precision weapons the military now uses rely upon GPS to insure they hit the right target. These include several of our rockets, bombs, and torpedo systems. Spoofing the GPS would render these weapons inaccurate, thereby mostly unusable. Viewed from a cost benefit perspective, the US spends about $18,000 for each of a particular kind of GPS guided bomb. Imagine how many cyber hackers can be trained for that same $18,000. Multiply that by an order of magnitude in the thousands, and you can see the advantage for the developing nation. Buy one bomb versus train and employ a team of hackers.
And finally, the scenario’s PLC attack is an echo of what was seen with the Stuxnet worm. After Stuxnet was isolated and identified, the rest of the world (i.e. those not responsible for its creation) was able to learn of its etiology. Stuxnet was designed to find a specific type of Siemens controller that the Stuxnet creators knew was being used in Iran to control their nuclear centrifuges. Although Siemens has much of the market worldwide, Rockwell International is very common in the US market. Now that Stuxnet is out in the wild, it would be easier for an antagonist nation to reverse engineer the capabilities of Stuxnet, and point them at the programming for a Rockwell control. If this worm could be used to knock the power out of phase for a larger electric motor or generator, then you get an Aurora Vulnerability. Like the Stuxnet attack in Iran, an Aurora Vulnerability causes physical destruction of the asset, not just destruction in the virtual world.
Although there is nothing available that specifically tells the story of how Stuxnet got into the Iranian centrifuge control system, it might be relevant to point out that the Iranian system is “air gapped” which means that it is not directly connected to any external network, including the internet. Using an air gap is a common method of foiling internet based intrusions. To illustrate vulnerability, refer to an experiment conducted by DHS. This experiment was designed to see what government employees would do if they found a disc or USB memory stick in their parking lot. 60% of employees plugged the found device into their work computer. If the device had an official seal on it, that number rose to 90%. Keeping this study in mind, how hard would it be to infect the host network (i.e. the municipal network, the company network)? Once the common network is infected, how long would it take before someone crossed the air gap with a now infected USB device, or how long before the laptop used on the common network is later used on the control network? Before you know it, the worm is in the control, awaiting action.
America is the only remaining super power in the world. As a result, it would be fool hardy to attack the US with traditional tools of war. Our enemies already recognize this, and are planning accordingly. The scenario outlined here does not require jet fighters, destroyers, helicopters, technological superiority, or even rifles. The war begins without firing a single shot.
We are pleased to welcome a new contributor to HLSR who has seen the evolution of security from the military, police and now homeland security education angles. Scott Winegar comes with experiences from a varied background. Scott has a BA from Portland State University in Administration of Justice. He was later selected by Department of Homeland Security to attend the Center for Homeland Defense and Security at the Naval Postgraduate School. There he was awarded an MA in Homeland Security.
Scott retired from the Portland Police with more than 27 years of service, achieving the rank of Police Captain. During his tenure with this agency, he served in a variety of roles, including patrol operations, investigations, gangs, hostage negotiation, personnel, and emergency management.
Scott also served 34 years in the military, most of which in the National Guard. He started his military career as a military policeman. Upon receiving a commission as a second lieutenant, he attended the Army’s Engineer School. During his years of service, he commanded a humanitarian aid mission to Jamaica, where his team built schools for several of the underprivileged villages in the country’s interior. He finished his years of service at National Headquarters in Washington DC. While there, he worked on a variety of issues, including critical infrastructure protection and intelligence. His duties also included deployment as the National Guard representative to almost all of the National level disasters occurring over the last few years. He helped coordinate the response for 4 hurricanes, 2 major wildfires, and finished by working at the Deepwater Horizon oil spill.
After retiring from the Portland Police, he accepted a job as second in command of the Portland Bureau of Emergency Management. He retired from that job to join the faculty at Concordia University-Portland, where he is Director of the Homeland Security degree program. We are thrilled to have Scott as a new contributor. The only problem will be deciding what sector with which to associate him! Welcome Scott!

Welcome to Homeland Security Roundtable! If you have been here before, you will notice that the site has changed. We have altered the look and feel of the site to enhance the overall viewing experience and to add some features for mobile devices. We have exciting new content on the way with new contributors and posts! We would appreciate any comments on the finish and functionality of the site. We will consider any adjustments necessary to provide our readers with a pleasant experience. Thank you!
Earlier this month I published a post about the disciplines of homeland security. The lists of disciplines were based on the work of Dr. Bill Pelfrey, a scholar and staff member at the Naval Postgraduate School’s Center for Homeland Defense and Security. Dr. Pelfrey has published a number of articles in his distinguished career in academia and has served in a number of administrative and teaching positions at prestigious institutions, including as Professor and Department Chair of the Department of Justice and Risk Administration at Virginia Commonwealth University (Dr. Pelfrey’s son, Dr. William Pelfrey Jr. also teaches at VCU). Dr. Pelfrey Sr. is also the author of The Evolution of Criminology.
After writing the July 2nd blog I contacted Dr. Pelfrey and asked permission to publish his article in its entirety, which he has graciously granted. The work from which I drew the disciplines of homeland security is thus attached.
Homeland Security Disciplines and the Cycle of Preparedness by Dr. William V. Pelfrey Sr.
Thank you Dr. Pelfrey!
It is widely agreed that certain public safety disciplines have a nexus to homeland security, and that individuals that are trained in and or practice these disciplines may (or may not) engage with partners in other agencies in a manner that can be described as homeland security, or what some have described as what homeland security might be. I have suggested in previous posts that the issuance of HLS degrees in higher education should be focused in the core disciplines of homeland security. Yet others have made the point, a valid one I believe, that homeland security is a discipline itself that by its very nature “binds together” the various disciplines for the purpose of responding to “all-hazards”. These points are great material for future posts. First, let us look at what disciplines have been or are often referenced as being associated with homeland security.
Researcher Dr. William V. Pelfrey developed a study in 2004 that described the disciplines related to “preparedness”. Pelfrey bases this summary on activities conducted by the former Office of Domestic Preparedness (ODP) in which focus groups were used to identify the key preparedness-related disciplines. The ODP identified ten key preparedness disciplines, the first four of which were considered primarily responsible for response and recovery. I believe that Dr. Pelfrey’s research provides one of the best supported listings of the disciplines of preparedness (Pelfrey, 2004):
|
Initial Disciplines |
|
| Law Enforcement | Emergency Dispatch |
| EMS | Health Services |
| Fire Service | Emergency Management |
| HAZMAT | Government Administrative |
| Public Health | Public Works |
In an effort to further define disciplines, Pelfrey identified additional categories, or as he refers to them “loose collectives of functional emphases,” that were identified as being related to preparedness (2004, p. 1). The disciplines or activities in this second group were identified as:
|
Secondary Disciplines |
|
| Business Continuity | Red Cross, Volunteer and NGO’s |
| Conveyances | Public Information |
| Cyber-security and IT | Media Management |
| Infrastructure Protection | Public Warning / Alerts |
| Homeland Security | Public Places / Major Facilities |
| Educational Institutions | Private Sector |
| Private Security, Loss Prevention | Financial Institutions |
| Major Event Security and Public Safety | Risk Management |
| Prosecutor | Transportation Services |
| Skilled Trades | Military |
This second group provides some insight into the issue of the wide range of homeland security-related activities. If it is possible to meet homeland security professionals from any of these disciplines, one can understand the difficulty in developing a common, specific definition of homeland security, which is why homeland security is often described in terms like “enterprise”, such as in the 2010 Quadrennial Homeland Security Review.
In my own research, I interviewed more than 20 individuals from Michigan that may be described as state and local homeland security professionals. Based on the results of these interviews, it appears that at the state and local level the homeland security core disciplines tend to align with law enforcement, fire, EMS, emergency management, public health, and government administration. Homeland security professionals often have focused expertise in one or more of these disciplines.
Pelfrey, W. V. (2004). Homeland Security disciplines and the cycle of preparedness. Unpublished Manuscript.
I believe the answer is a resounding “maybe”, at least at this point in history. However this question might be better answered by looking at two related questions. These are:
- What is a professional?
- Are homeland security practitioners professionals?
What is a Professional?
Max Weber, a German sociologist and philosopher addressed the concept of professionalism in an essay examining politicians that provides a uniquely appropriate corollary to the homeland security professionalism issue. Weber described “occasional” and “part-time” politicians, as persons who engaged in politics occasionally (such as voters) or slightly more often for personal gain. For Weber, a “professional politician” was one that “lives for” or “lives off” of politics. In a 1978 translation of Weber’s essay entitled, Politics as a Vocation provides the context for the term professional:
…the prince could not make do, of course, with these merely occasional or part-time assistants. He had to seek to create from himself a staff of assistants wholly and exclusively dedicated to his service, thus professionals. (Gunlicks, 1978, p. 500)
Using the Weber criteria, homeland security practitioners that are “wholly and exclusively” dedicated to service in homeland security could be “professionals”.
Federal employees of the Department of Homeland Security operate in an environment in which homeland security activities comprise 100% of their daily activities. In the federal department, homeland security is well-defined by statute. Congress has passed laws creating, defining and specifying the role and activities of homeland security via the department.
At the state and local level the homeland security practitioner is less obvious. HLS is often practiced at the state and local level by individuals with a variety of duties whose background, education and experience are related to one or more of the homeland security disciplines. We will identify and discuss these disciplines in an upcoming post.
Are Homeland Security Practitioners Professionals?
Based on the Weber criteria, federal employees of the Department of Homeland Security may well be homeland security professionals. But outside of the department of the national government homeland security is not clearly defined. As a discipline, it is unclear that homeland security is, in fact, a profession. It is certainly not on par with one of the “learned professions” which are generally defined as the practices of Law, Medicine and Theology. Are references to “homeland security professionals” outside of the federal government appropriate? Does one understand clearly a person’s expertise when they are described as a homeland security professional?
Part of the difficulty with the vagueness of homeland security is the inability to understand what qualifications or skills homeland security professionals possess. This difficulty is enhanced by two major factors. First, homeland security is a U.S.-based term and concept, and second that there is a lack of recognition that other enterprises have resolved vagueness within their own disciplines by emphasizing the core disciplines of their enterprises, as exemplified by the healthcare industry.
Homeland security is a largely American development, used to describe an element of U.S. national security policy and strategy. It is not common to find the term “homeland security” in regular use by countries other than the U.S. To reinforce this point, a simple internet query can be conducted.
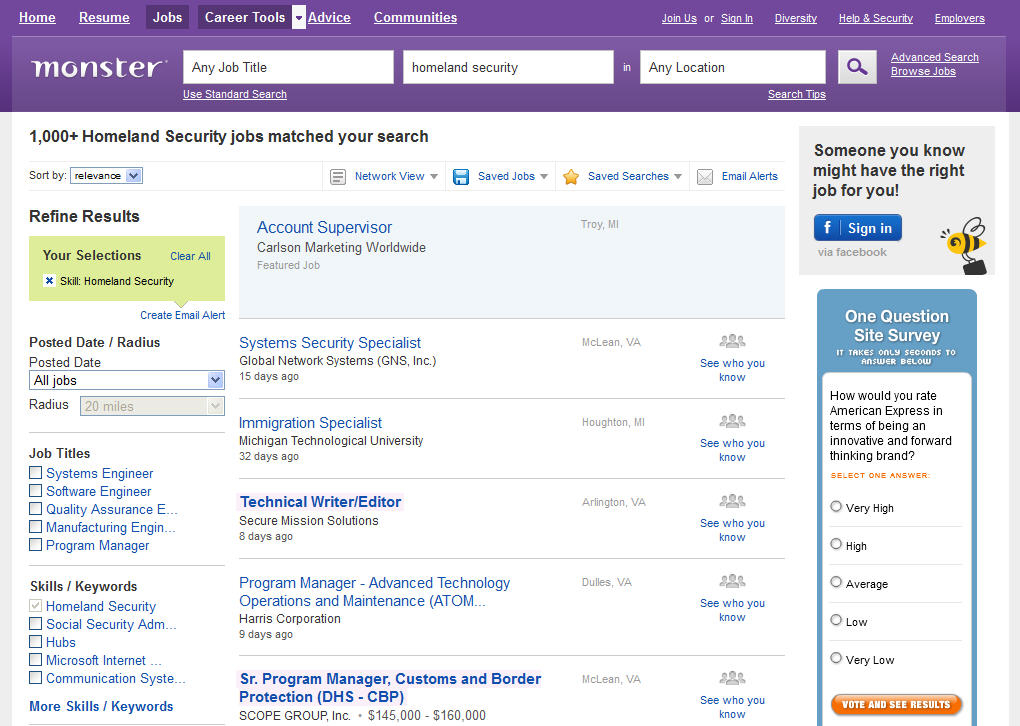
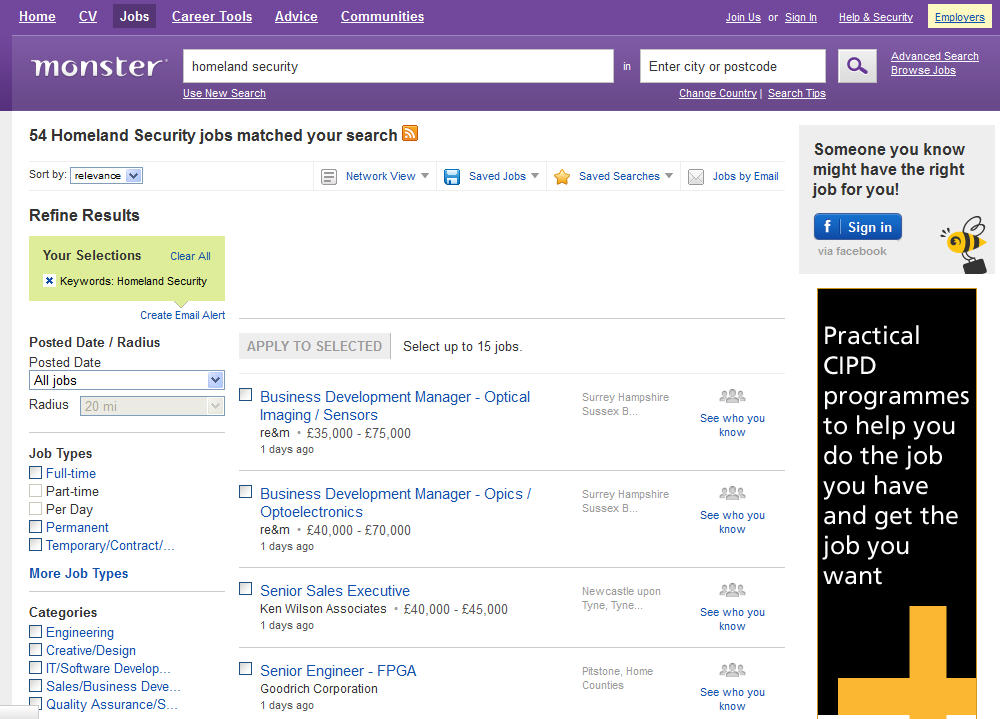
The following screenshots represent internet job search results on Monster.com’s sites related to several English-speaking countries. Note the results when a keyword search is conducted using the term “homeland security”:
As indicated, the US-based search provides thousands of returns while the Canadian and UK searches yield only a handful of returns which are often from US-based companies. Homeland security is a US term, and may not mean the same thing in the rest of the world. What does this mean for individuals getting homeland security degrees at US universities? Can they only work in the US? This should be considered by any university or student considering involvement in homeland security degree programs.
The “Healthcare” Example
The term “healthcare” describes the large and diverse array of services related to the maintenance and restoration of the health of people. All persons and jobs that have a nexus to the health of humans are healthcare professionals. One can be in healthcare and not be a doctor; however, there is no way to be a medical doctor and not be in healthcare. There are no “healthcare” degrees at colleges, but there are degrees in healthcare administration and nursing. Because of the broad meaning of the term “healthcare,” there is not sufficient specificity to develop a degree specialty—one has to study the particular discipline or specialty within the broader category.
It might be said that homeland security is a general term and not a specific discipline. Just as there are healthcare professionals, it might be possible to be a homeland security professional if one has expertise in a related discipline.
Conclusions
It is interesting to consider that, as a homeland security professional, one might be an emergency manager, but to be an emergency manager, one does not necessarily have to call oneself a homeland security professional. This dichotomy indicates that homeland security is a term that may be used, or not, depending on individual preference. I have interviewed emergency managers that call themselves homeland security professionals because it “sounds like a better job”! Conversely, I know emergency managers that feel that homeland security is not a real discipline.
“Homeland security professionals” do not exist in the same way that “professional engineers” exist. In most states professional engineers must meet a set of standards and pass state-administered examinations before being certified a “professional engineer” or allowed to use the initials “PE”. The current lack of standards or certification is not meant to imply that homeland security officials are unprofessional or lacking abilities. It is important to recognize that homeland security is a field that requires specialized knowledge and expertise.
Based on my experience and research, federal level employees of the Department of Homeland Security might be defined as “homeland security professionals”. At the state and local level, the term is largely a matter of preference and does not have significant meaning in today’s environment. Internationally, the term is not commonly used. These issues must be resolved by the further development and institutionalization of homeland security as a specific discipline, otherwise homeland security is destined for the same fate as Civil Defense.
Gunlicks, A. (1978). Max Weber’s typology of the politicians: A reexamination. Journal of Politics, 40, 498–509.This week at HLSR we are pleased to welcome a guest blogger, Nick Catrantzos. Mr. Catrantzos is an adjunct professor of homeland security and emergency management at the University of Alaska, Fairbanks, and a recently retired security director who, post-9/11 oversaw a $30,000,000 capital investment in security technology, including surveillance cameras, for a large public institution. Nick Catrantzos is the author of No Dark Corners: Managing the Insider Threat available from publisher CRC Press at Amazon here.
We at HLSR are a fan of Nick’s writing and have benefited from his expertise via his All Secure blog. Nick is a graduate of the Naval Postgraduate School’s Center for Homeland Defense and Security (CHDS) and wrote an award-winning thesis upon which his book is based. This article, written and published in blogs before, has been shared extensively with our partners in the security industry. Surveillance cameras are often thought of as a security panacea. Nick reminds us that not every security problem is measured in pixels…
Maslow’s Hammer and the Double-Edged Sword of Security Cameras
By: Nick Catrantzos
(Originally published as See More Nails? Get More Hammers, September 13, 2011, on All Secure blog, http://all-secure.blogspot.com/2011/09/security-video-see-more-nails-get-more.html. Subsequently published as Maslow’s Hammer and the Double-Edged Sword of Security Cameras, September 20, 2011, on HLS Watch blog, http://www.hlswatch.com/2011/09/20/maslow%E2%80%99s-hammer-and-the-double-edged-sword-of-security-cameras)
Specialists see the world in terms of their specialty.
Every time an attorney specializing in litigation or a vendor specializing in camera sales opines about the relative merits or perils of security surveillance, their natural bias competes against respective areas of ignorance to limit the value of their attending pronouncements. Either may have colorful things to say. Both omit points important for a deeper understanding of the issue.
Beginning with the lawyerly lament about too many cameras not only impinging on individual privacy but potentially leading to profligate spending in a time of fiscal constraint, the useful analytical point submerged in this hackneyed observation needs only a little more digging to unearth. The unstated point is that any flawed implementation is likely to waste money and produce unintended consequences undermining its desired benefits. Too much of a good thing can kill, hence the double-edged sword of elemental boons like fire and water, which await only arson or storm surge to turn from life-savers to life-extinguishers. So, yes, too many cameras multiply the potential for abuse, for someone using them to nefarious purposes, whether in adjusting fields of view to look not at the parking lot where assaults occur at night but at a nearby residence in whose yard a teenager is sunbathing immodestly during the day. Waste is also likely, particularly if the absence of intelligent oversight means that a security camera vendor receives carte blanche to clear the warehouse of every high-end, pan-tilt-zoom, infrared, weatherized camera in an installation where three quarters of the cameras could have easily been fixed-position devices costing a fraction of the price and requiring significantly less maintenance. The vendor gets a bonus for exceeding sales targets, while the customer gets an impressive quantity of modern devices to demonstrate how serious the end user is about security. Win-win, or lose-lose? More on this soon.
As for Maslow’s hammer, …
It comes from what the psychologist and founder of the hierarchy of needs once observed when noting that if one’s only tool is a hammer, one sees every problem as a nail. Rare is the special product vendor who can see or propose any solution other than his or her stock in trade. Thus, to the average security camera vendor, there is no security problem that cannot be solved without the addition of another surveillance camera. By comparison, an average purveyor of guard services tends to do precisely the same, only with services instead of products. Thus, to the latter, every security problem is just another guard assignment away from being solved. Each provider is selling only a hammer, therefore each sees the security problem only as a nail.
What is the real solution to this institutionalized myopia borne either of over specialization or limited range of implements in one’s tool chest?
The answer is the kind of infusion of mind into the swirl of events that requires a seasoned managerial or security perspective, and preferably both. What do seasoned professionals do when facing security surveillance as a management issue? They begin with objectives, focus on the results their organizations need to achieve, and defend against scope creep or one-off distractions that enfeeble the chances of attaining identified objectives. This approach, incidentally, applies equally to technology implementations unrelated to security. Why? Because champions of new systems invariably oversell and continue to offer product and service extensions, often with little regard for whether their initial offerings have satisfied original criteria. If your security camera implementation has done nothing to limit parking lot assaults, for example, the vendor may well propose adding more cameras to more places, including hidden cameras outside of reception areas and extra ones at entrances and exits. Similarly, if your guard force contractor has failed to deliver on advertised loss reductions, he or she may suggest more guard posts and patrols, and even using uniformed guards as lobby ambassadors in reception areas.
See more nails? Get more hammers.
Here is why this cycle of repetitive failures turns into a lose-lose situation.
Both provider and beneficiary have lost sight of original objectives and, quite often, neither had thought these objectives through in the first place.
What needs to happen instead?
Begin by deciding the larger objective.
Are the security cameras intended to prevent loss or to apprehend adversaries after the fact? A serious answer to this question guides the entire scope and investment of the surveillance camera implementation effort, and it is only a fool who will ask the hammer seller for a tool selection that also includes screwdrivers, pliers, and saws. Of course the vendor will offer to do it all. Turn on the blue light; the man wants a blue suit. But the reality is that attempts to do it all invariably end up diffusing effort, overextending systems, budgets, and schedules, and delivering flawed implementations, resulting in strained customer-provider relations. You can do one thing well or all things badly. What does your organization need?
Assume your organization is more interested in prevention than apprehension.
This is the private sector security model as contrasted with the public safety model. The latter has a societal objective of chasing down offenders to capture and punish them and, by doing so, demonstrate to society at large that crime does not pay. [Incidentally, this public safety bias limits the ability of most police to operate surveillance cameras solely for prevention. Their invariable tendency is to use them more for investigation. Also, because they hired on to chase malefactors, watching cameras or defending assets are unattractive to cops in their prime.] In the context of running a business or even a public institution, however, few organizations can afford the resources for this hunt. Instead, their security functions earn their keep by preventing losses – which cost significantly less in time and staffing than trying to shadow the responsibilities of a police force without the same powers of arrest or investigation.
How does this assumption affect security camera implementation?
First and foremost, if you are interested mainly in prevention, then you optimize your surveillance system for intrusion detection, period. This means that you place cameras along perimeters and entry points, and reduce to an absolute minimum the impulse to stockpile data unrelated to intrusion. This means you do not warehouse video images for months or years at a time because they may come in handy in some event reconstruction or one-off investigation into something at some point in time. Someone in the organization will always make the case that such capabilities are nice to have. But that someone will be an individual or department that has no idea of or responsibility for the burden of keeping such data, in terms of staff hours and capital investment. Absent a regulatory requirement that compels you to do otherwise, you must decide whether you are in the prevention business or in the monitoring-to-help-everyone-else-out business.
If in the first, you overwrite your video files at the first logical opportunity – perhaps a week or two – and keep only what you flag for retention – perhaps within a few days of a loss or suspicious incident. This protocol puts you squarely in the prevention business rather than in the internal snooping business. It limits the audit trails that institutionalized snooping occasionally seeks, however. This means that the supervisor too inept to monitor or discipline an underperforming employee will not be able to look to your surveillance system to say, “Aha, Harry isn’t showing up on time and is always leaving early on days when I have to go out of the office.”
What will such supervisors have to do if the surveillance system is unavailable to supply evidence to back disciplinary action? They will have to do the same thing they had to do in the days before such a system was around: supervise. Indeed, an employee relations manager told me that any time a supervisor wants to rely on security audit trails to catch an employee in some kind of routine performance deficiency, this proclivity signals a lack of supervision.
It is no surprise that specialists seeing the world in terms of their specialty offer up flawed solutions, without necessarily doing so in bad faith.
They have hammers, so they see nails.
The finesse in vaulting over this common hurdle, when it comes to security surveillance cameras, is in looking past the myopic vision of the hammer sellers to understand the bigger picture. Although it is rare to find this capacity in specialists, it is not entirely absent. I have worked with the occasional security systems vendor – usually a seasoned one who is secure in tenure and sufficiently senior in the organization to be insulated from sales quotas – who can and will advise against more cameras than anyone can usefully monitor. Such advice benefits the client and serves the enlightened self-interest of the provider.
Every customer appreciates a hammer seller with the nerve to refuse to sell you another mallet when you clearly need a screwdriver.
Special thanks to Nick Catrantzos for allowing HLSR to publish his article.